Cyber Security (Total Posts : 19 )

How can avoid malware from a PDF file ?
PDFs can contain harmful security threats such as viruses, malware, and trojans. Like many other file types, PDFs can be used to compromise our data and sensitive information if you do not take the proper precautions. We save most of our documents like educational, banking...
Read More Published on : 1 week ago
What is spyware and How to avoid this ?
Spyware is a type of malware that monitors your phone's activities without your knowledge. Spyware on Android can be a result of wrong app downloads. It can be installed by another person. One of the dangers of spyware is that it can collect browsing...
Read More Published on : 2 weeks ago
Cyber Slave Report : Ravi was kidnapped and Trapped in the camp of cyber slavery and Many other people have been also cheated online
24-year-old Ravi from Sri Lanka went to Thailand for an IT job. However, instead of working in a high-rise office in Bangkok, he was trapped in a dark complex in Myanmar. Ravi was kidnapped. Then he was taken across the river near the Thai border...
Read More Published on : 1 month ago
How to Avoid Digital payment scams
Digital business has made our life easier. Digital payments are easy, fast and secure. But on the other hand, it has also increased the rate of online fraud.In the last few years, there has been a significant increase in cyber...
Read More Published on : 1 month ago
Cyber crime in Nepal : 6 times increased crime incidents with in 5 years
In the last five years, the incidence of cyber crime has increased by six times. According to the statistics of the Cyber Bureau of Nepal Police, in the financial year 2076/77, there were 2,301 complaints related to cyber crime, while in the current fiscal year ...
Read More Published on : 1 month ago
Free Cyber Security Training for 4 thousand people by Kathmandu Metropolitan City
Kathmandu Metropolitan City is going to provide cyber security training to 4 thousand people. The goal is to train 15,000 people and get 5,000 people employed under the 'Employment and Income Increase, Kathmandu's Prosperity' scheme. It is going to cooperate with this council and Gap...
Read More Published on : 4 months ago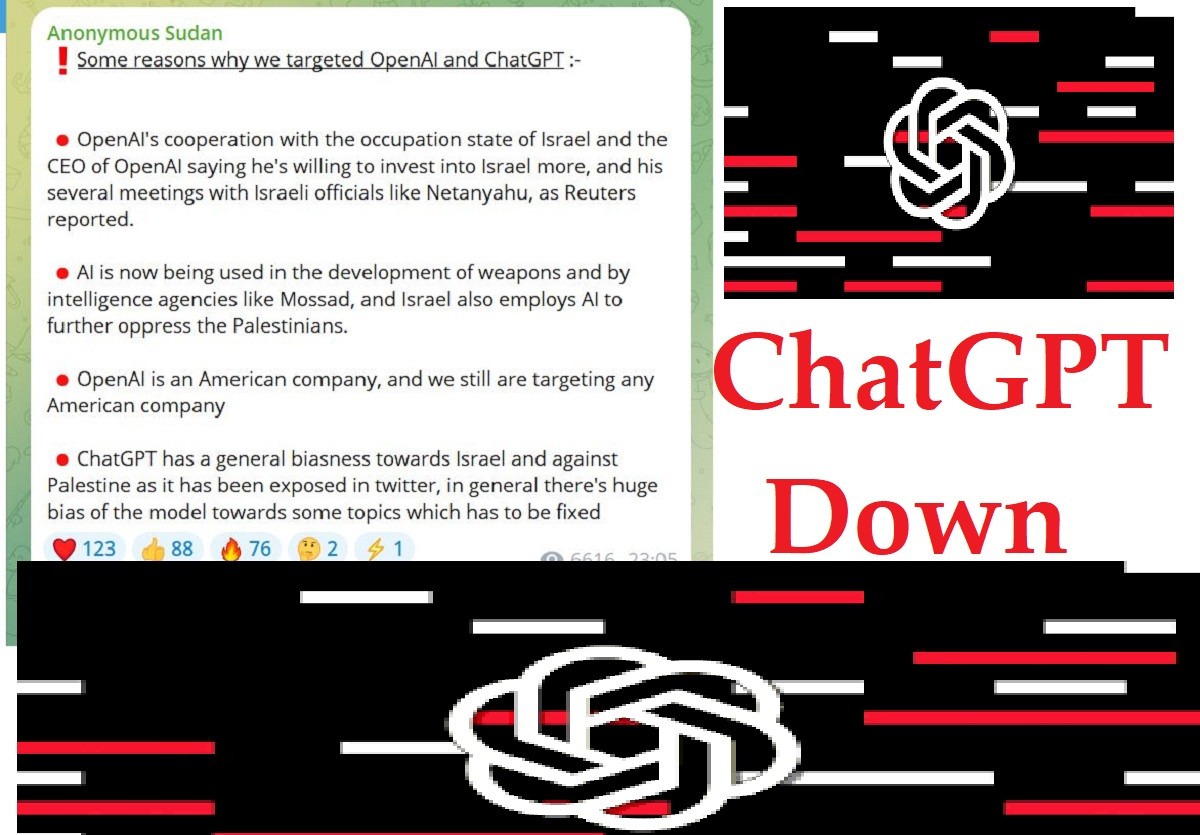
CHATGPT using Email ID public by hackers
The e-mail ID used to run ChatGPT has been released by the hackers. The research team of Indiana University Bloomington has issued a security warning about the most powerful model of ChatGPT, GPT 3.5 Turbo, and said that the email ID of users using ChatGPT...
Read More Published on : 4 months ago
What is 'SQL injection' used in cyber attacks and how to avoid it ?
Some people use such code in the context of computer, so that all the data of your website or even admin access is accessible to them. This is called SQL Injection (SQLi). SQL injection is a type of cyber attack, where a hacker makes a...
Read More Published on : 5 months ago
Why ChatGPT is down ? Anonymous Sudan Hackers Claim Responsibility
OpenAI's ChatGPT is affected in most parts of the world. According to the website down detector, which evaluates the website down, the website was down for three hours. According to OpenAI's status checker, the platform has recently been affected by unusual traffic. It is...
Read More Published on : 6 months ago
SIM Swap Fraud in India : What is SIM-Swap Scam ?
SIM-swap scams are on the rise. Fraudsters manipulate network providers to associate the victim's number with a SIM card under their control. In light of this incident, citizens should remain vigilant and adhere to preventive measures to safeguard against such fraudulent activities.
Read More Published on : 6 months agoPopular Posts
-
7 months ago 6713 views
-
1 year ago 4169 views
-
2 years ago 4141 views
-
11 months ago 3824 views
-
7 months ago 3237 views